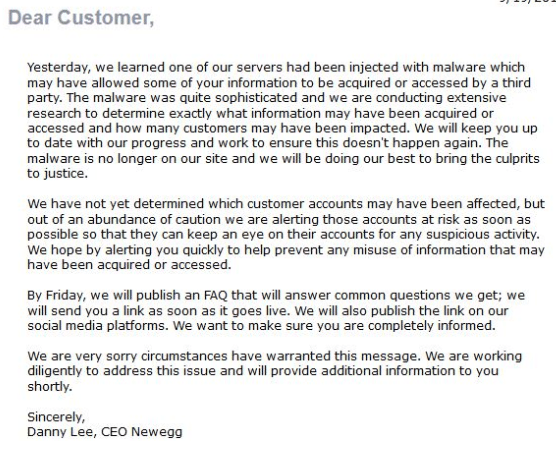
Newegg is the latest to be affected by a data breach. Hackers inserted skimming software (Magecart) into Newegg’s payment page between August 14th and September 18th, 2018. Newegg has sent out an e-mail to customers stating they don’t know exactly which customer accounts have been affected yet and that by Friday they will publish a F.A.Q. answering common questions. For more details on the attack itself I’d recommend reading the reports by Volexity and RiskIQ.
Whenever a breach like this happens I always say that the consequences for data breaches need to be increased as currently they are occurring far too frequently and it’s apparent companies aren’t spending enough time and resources to prevent these types of attacks.







I used my credit card during the British Airways hack, and around 2 weeks later someone used my credit card to buy $6,000 worth of beauty products. The strange thing is that the beauty products were shipped to my house. I don’t understand, why would the crooks steal my credit info and then ship stuff to me?
They were either going to wait outside and take the boxes, or the checkout default was to ship to the billing address, and they forgot to change it
Excited to receive Newegg’s apology, commitment to never allowing this to happen again, and complimentary year of credit monitoring adding to my 125 years of consecutive monitoring from the previous 150 other company breaches that **may** have affected me.
Cannot f’n believe Newegg got BREACHED. Does it count as poetic justice that a cool, hip, geeky, techy, California company catering to coders gets BREACHED? This coming from a guy who loves Newegg BTW.
Just wait till Amazon gets BREACHED. Then the sheep may finally wake up and smell the coffee.
Anybody wanna start a cybersecurity software company with me? At this point the demand for good solutions has got to be through the roof, a good app could make us millions in no time.
A lot of the “top” cybersecurity companies actually use military-style approaches to data protection, clearly it’s not working well enough, perhaps a more civilian-style approach is needed.
Good luck selling your services. The reason these breaches happen is because selling security is hard. It’s 1.) Very expensive 2.) Very complex 3.) Very burdensome
Ever talk to one of these groups? First thing they say is you need to completely blow away your entire network, rebuild it using latest standards, because it’s assumed to be compromised. The price tag of such an approach is astronomical. These companies ultimately make all their money coming in after a breach to do comprehensive audits and revamps.
Even the best companies with money in their IT budgets will try to figure out exactly where they “have” to be and jump over that bar only. In the end we need to assume servers and databases will be breached. This means securing payments as point in time transactions and ensuring no personal information is ever stored unless absolutely necessary.
Parkerthon, 100% agree on the complexity, cost, and risks associated. Securing data is not only difficult, but is incredibly expensive and wrought with liability issues. And yes these cybersecurity teams always preach that the BREACHED company needs to blow it up and rebuild, and rebuild with that cybersecurity companies costly solution.
But when is enough enough? Does the government have to get involved? I get it that I shouldn’t store my personal info unless I absolutely need to. But something has to change because these BREACHES are terribly damaging to the consumer and they are happening left-and-right, all day all the time it seems.
Perhaps a SAAS product with an insurance component?; I dunno just thinking out loud. I’m just sick and tired of the BREACHES, and in general the widespread lack of privacy.
I used PayPal during this time and based on the released info (surprisingly detailed) I should not be affected since the malicious code was inserted into the shopping cart page and scraped entered credit card data. Since PayPal uses an external token it would not be be impacted by this breach.
So if you had a saved payment method on your Newegg account, and didn’t manually enter the CC info, you are safe?
no because saved data was still transferred.. If you made a purchase on newegg through their portal, you should be concerned about that Cc’s info.
Hope they’re sued. Sure, server security isn’t as cheap as a Norton subscription, so I figured it was one line-item they decided to axe off the proposal when buying their servers as a cost-cutting measure.
Actually, the Comodo CA may be liable since they issued a “Newegg” certificate for the falsely registered domain. More info is needed regarding the verification level, etc. but that is looking very bad for them.
Essentially, from what I understand so far, Comodo issued an SSL certificate stating that neweggstats.com was owned by Newegg Inc. so the web browser would not show certificate errors (unsecured elements contained on the page).
Although, Newegg.com does not use an extended validation (EV) certificate, so there may be no fault by Comodo. A non-EV certificate will validate SSL as long as the requester can prove domain ownership (such as via DNS txt record). Certificate extended validation must prove that the requester is the company itself and are typically represented in the web browser by displaying the company name as a prefix to the URL.
Most users won’t notice or care if it’s EV or not–I consider a user responsible enough if they don’t intentionally click through the big red security errors because it’s the only way they can complete their transaction.
Wow…did the McAfee Security subscription for the Newegg servers expire or something? Don’t they know they can get that free after rebate from Frys.com?
Probably an employee did it.
LOL
TL;DR: They captured your payment info. Name, CC #, Exp date, CVV. Basically siphoned off all the fields you filled in to pay for a Newegg order you placed in this time frame. You absolutely should have any CC you used with newegg in this time frame closed and reissued at the very least.
My question is whether previously saved card information is okay.
No based on the information it skimmed data going to the final “payment processing don’t hit back or close out page”
So saved data isn’t the problem… only cards that were paying.